This article helps you understand the WordPress website security threats on the internet in 2021
Living in the modern era, the internet has become an indispensable tool at our disposal. We have become so used to it that it’s hard to imagine the time when the internet did not exist. The internet has introduced unrivaled ease into our life.
Along with this ease, it has also become a hub for crimes and underhanded activities.
“For every lock, there is someone who is out there trying to pick it or break in”
– David Berstein.
Stories of WordPress websites being attacked and information being put at risk are nothing new to us. These things have been around since the advent of the internet. Keeping the statistics in front of us, we can say that our information and WordPress websites have also been compromised regardless of whether they are in our knowledge.
To give you a better perspective of the current state of WordPress website security threats, we have put together some of the most common WordPress website security threats out and about the internet. These are the things you need to be most aware of as you go about your business on this vast internet. Here is a list of some potential Security Threats:
Ill-intentioned Employees
Some employees hired by the company might not have all the right intentions at work. They can leave the company vulnerable to many kinds of attacks due to their ill intentions, as their negligence or hostility can leave the company in huge trouble.
Statistics show that data breaches of companies broke out 48% of the time due to the negligence of the employees. 95% of online protection breaches are brought about by human blunder.
These statistics leave us with the impression that the employees’ negligence remains one of the biggest WordPress website security threats.
Broken Authentication
Broken authentications are the weaknesses or loopholes that allow an attacker to enter/bypass the WordPress website’s authentication method, exposing the website’s security.
They often occur due to issues like weak or easily guessed passwords, ineffective multi-factor authentication, non-rotating session IDs after successful logins, etc. Broken authentications are a gateway to a plethora of security threats.
Several changes to the security features can resolve this security factor. Implementing multi-factor authentications, implementing weak password checks, aligning password strength, complexity, rotation policies, and harden the API pathways against account enumeration attacks by using the same messages for all outcomes are just some of them.
Sensitive data exposure
As the name suggests, it is a sensitive topic and requires encryption at all times, even when in transit. Leaving sensitive data exposed can be very harmful to WordPress websites, WordPress website reputation, and security management.
Sensitive data such as credit card numbers or user passwords should never be left unencrypted. Otherwise, it will be at risk of exposure.
Shred the unimportant sensitive data and never keep encryption keys next to protected data. Data exposures have become one of the most common security threats.
Sensitive data breaches uncovered 36 billion records in the first two quarters of 2020.
Cross-Site Scripting (XSS)
Cross-Site Scripting attacks are a type of injection through which scripts of malicious nature are injected into trusted WordPress websites. These attacks occur when an attacker sends malicious codes to the end-user using a web application. They have become a significant security threat in recent times.
These attacks are successful due to the flaws in different web applications.
Attackers can use XSS for carrying out their malicious acts with the users. The end-users generally have no idea whether the script should be trusted, as they think it comes from a trusted source.
When the malicious script is successfully in the user’s browser, it can gain access to any cookies or sensitive information; even the content of the HTML page can be re-written by these malicious scripts, posing a very high risk to the security of data.
However, the user can use specific techniques to avoid cross-site scripting vulnerabilities.
The extent of XSS of all web application attacks has developed from 7% to 10% in the first quarter of 2017. For as far back as four years, XSS weaknesses have been available in around half of the sites.
Insecure Direct Object References (IDOR)
If a blind eye is turned towards all the user inputs, it can cause serious plugin vulnerabilities.
When the WordPress website uses the user-provided input, attackers can expose the data, gain access or do things that should be hindered. IDOR can take place in many forms whenever user-controlled parameter values are used to access the functionality of the WordPress website/application.
For example, a code has a .php module that lets the user download files, but the code authorization failed to be included by the developer.
The attacker would now download any system documents that the user approaches, similar to the application code itself or different data left lying around on the server, identical to backups.
IDOR can be prevented by performing regular, proper, and consistent user authorization checkups. The whole concept of IDOR can be avoided by adequate storage of data internally and not relying on it being passed from the clients via CGI parameters.
Security misconfiguration
Security Misconfiguration is characterized as neglecting to carry out all the security controls for a server or web application or executing the security control; however, doing so with errors.
An organization considered a protected environment has hazardous gaps or mistakes that leave the WordPress website open to chance.
A typical WordPress website security threat is the poorly misconfigured security system like running the application in production with debugging enabled, running outdated software, not changing default keys and passwords, having unnecessary services on the machine, etc.
Developers can prevent these by having a good process that can run tests on deployment to run as soon as the deployment.

Between January 1, 2005, and May 31, 2020, there have been 11,762 recorded data breaches.
Unvalidated redirects and forwards
This is one of the input filtering issues. A target site has to redirect a URL module as a getting parameter and later redirects the browser to a malicious WordPress website.
Users will click the URL when they see it. They would have little to no idea about the redirection or its security threats or plugin vulnerabilities, exposing them and their sensitive data to the malicious WordPress websites or the attackers who have bad intentions regarding them.
These can be prevented through various checks and opting not to do redirects at all as they’re of little necessity. The authorizer should safelist user-defined parameters and have a static list of valid locations to redirect to.
1 of every 13 web redirects leads to malware. Most malicious domains, about 60%, are related to spam campaigns.
Website malware families and other notable WordPress website security threats:
“Beware of geeks bearing gifts.”
― Kevin Mitnick
Website malware or malicious software is that which is written with the intent of bringing harm to data. Website malware is of different types, including viruses, trojans, file-less website malware, ransomware or hybrid attacks, etc.
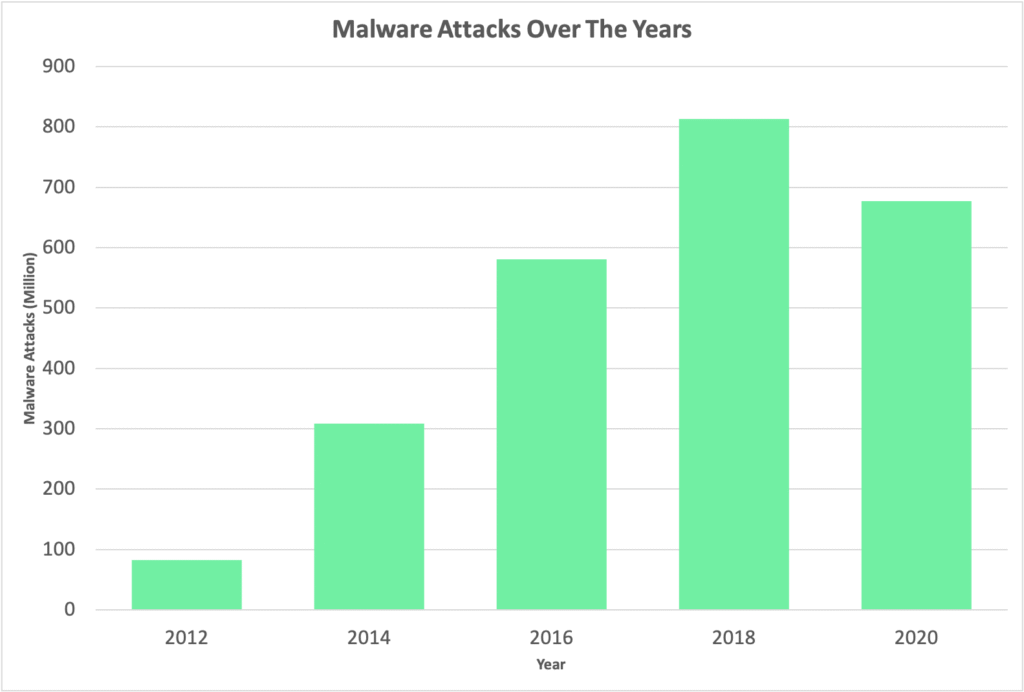
In 2018, 812.67 million infections were caused by website malware. Another interesting fact about website malware is that 92% of the malware is delivered by emails. The top malicious email attachments are .doc and .dot, which make up 37%. The following most noteworthy is .exe at 19.5%. But in recent years, website malware has been decreasing steadily while WordPress website hackers have been shifting to other modes of attack.
Website backdoors
Website backdoors are means to access the WordPress website’s encrypted data or the system by bypassing the original security mechanisms of the website.
Developers create them for troubleshooting purposes; however, attackers sometimes exploit them to gain access to the WordPress website’s internals.
Backdoors can pose a risk or a WordPress website security threat and its available data. Attackers place website backdoors. Usually, through malware, a malware may act as a WordPress website backdoors itself, allowing other malware modules that would further carry out the actual attack.
Website backdoors are usually challenging to detect, but antimalware software might be able to see them. Website developers can use several strategies to avoid WordPress website backdoors attacks like application firewalls which might help detect and block them.
SEO Spam
SEO spam is also known as Spamdexing. It is an attempt to use your WordPress website for ranking content that won’t rank by itself or otherwise.
WordPress website hackers use this technique to generate SEO ranking and revenue, but meanwhile, they would destroy the WordPress website itself through spamming. SEO itself is not considered spam, but some tactics implementing SEO tactics are a red flag.
If somehow Google can detect SEO spam, the WordPress website becomes at risk of being permanently banned by Google, making SEO spam very dangerous.
WordPress website hackers break into the WordPress website through outdated plugins or by weak credentials. They would then rank or promote their products using your WordPress website and by spamdexing.
SEO spam can be detected by various techniques, including warnings in the Google search console, sudden changes in traffic and unexpected ads, etc.
SEO spam removal plugins can aid in clearing the SEO spam from the WordPress website and help prevent future attacks.
SQL Injections
SQL injections are WordPress website security vulnerabilities that allow the attackers to interfere with queries made to the database by the site. It generally permits an attacker to see information that they are not typically ready to recover.
SQL injections may incorporate information with different users or whatever other information the actual application can get. An attacker can adjust or erase this information, making ongoing changes to the application’s substance or conduct.
In certain circumstances, an attacker can heighten a SQL injection assault to think twice about the virtual server or other back-end infrastructure or play out a denial-of-service attack. WordPress website hackers can adjust or erase the information or even award themselves administrator access.
Distributed Denial of Service (DDoS)
DDoS is a subset of DoS (Denial of Service) attacks. It is a malicious WordPress website security threat that WordPress website hackers employ to overwhelm a website with fake traffic or requests to the database from an interconnected web of devices referred to as a botnet. DDoS has the impact of tying up all accessible assets to manage these requests and crashing the webserver or diverting it enough that typical clients can’t make an association between their computers and the WordPress website server.
The first DDoS attack can be traced back to Khan C. Smith when he crashed internet access to the Las Vegas Strip in 1997. Canadian teen hacker Michael Calce performed the feat of hitting Yahoo!, Amazon, CNN, and eBay within a week in 2000 by DDoS attacks.
DDoS itself does not steal one’s data. Their principal purpose is to slow down service while using a botnet. The botnet (Interconnected Network of Devices) communicates with a Command & Control Server to unleash a horde of devices upon the WordPress website. By this method, a DDoS attack unleashes its primary target, which acts as a veil for other malicious acts.
You can view the real-time DDoS attacks dashboard.
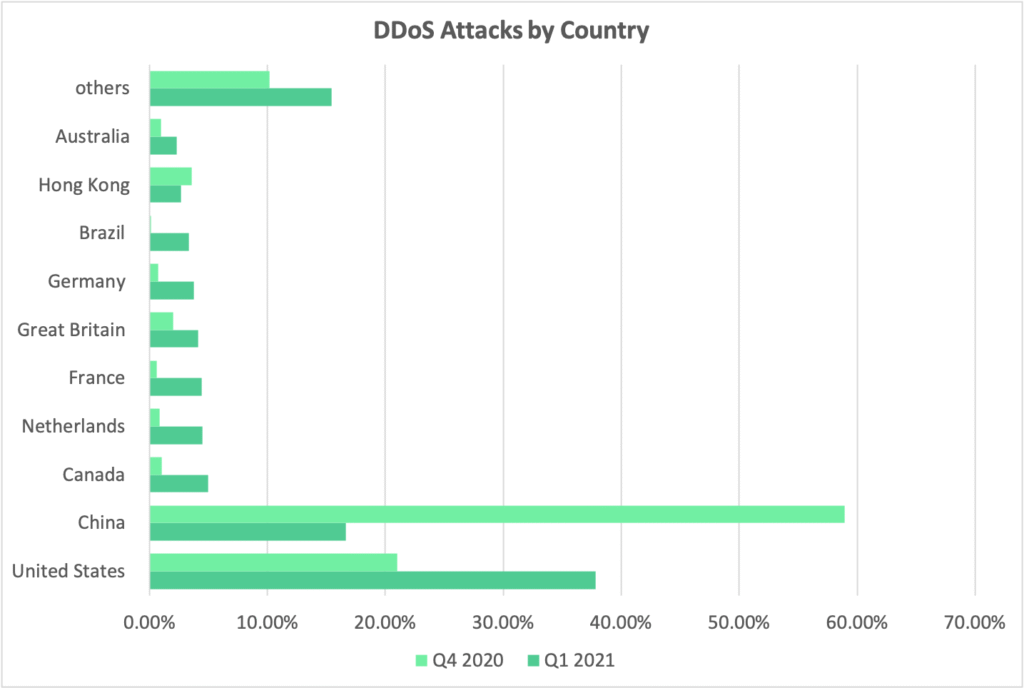
By 2023, the complete number of DDoS assaults worldwide will be 15.4 million. Attacks on IoT (Internet of Things) gadgets significantly increased in 2019. IoT devices experience 5,200 assaults each month usually.
In Faburay 2020 Amazon AWS mitigated the biggest-ever-DDoS attack clocked a massive 2.3Tbps. Amazon disclosed the DDoS attack details in AWS Shield Threat Landscape [PDF].
Hack Tool
Hack Tools are a branch of riskware (Risky Software) employed by WordPress website hackers to exploit the vulnerabilities of your WordPress website and hack into it. They are not malicious nor are riskware in general, but they pose a particular risk, such as creating website backdoors, which gives the invaders control of your device.
Hack Tools are often downloaded from ill-reputed websites under the guise of cracked or free software. When they are installed onto your device, they leech into your computer and perform their purpose. After the invader has taken control of your device, the symptoms of a virus become apparent.
Website Defacement
Website defacement is breaking into WordPress website sensitive data As a server and hosting a separate website on it. It has usually been done to promote a message, diminish the SEO ranking of the hacked WordPress website, and boost the ranking of another website. More recently, it has been used to upload website malware or spyware. These can be forced upon unwary users who visit the WordPress website.
This website malware and spyware cling to the user’s device, so the WordPress website hackers infect several computers without giving the slightest notion to the user.
Third parties can access your web server due to many reasons;
- An SQL Injection
- Cross-Site Scripting (XSS)
- DNS Hijacking
- Website malware
Some major defacement attacks of the 21st century are:
- The NHS (National Health Service) Website in 2018
- Google Romania and PayPal Romania in 2012
- The 15,000 Websites of Georgia in 2019
Phishing
Phishing is the crime of deceitfully manipulating a person to extract their personal information, such as credit card numbers and bank accounts. The term ‘phishing’ derives from “Phone” and “Fishing.” Like fishing, the hacker sends an e-mail or a message from an imitated trusted source. The person opens the mail and finds a dire condition that must be remedied or risk a consequence. If the person is persuaded by an e-mail, he will be redirected to a fake website of a trusted company, such as the person’s bank. The person will be asked to enter their credentials, easily stolen or auctioned off to the highest bidder.
Phishing is the simplest kind of cyberattack and, at the same time, the most dangerous and effective
– Adam Kujawa (Director, Malwarebytes Labs)
Phishing is more straightforward than other cybercrimes because one does not need to pass through multiple layers of security. A hacker employs social engineering to deceive their targets. Sending e-mails is much easier than figuring out a method to surpass the security standards on modern-day WordPress websites.
There are multiple types of phishing to be witnessed on the internet. Some examples are:
Clone Phishing
The attacker clones a legitimate e-mail that had a hyperlink attached to it. The WordPress website phisher replaces the link to a scam website to phish a person.
Phone Phishing
Phone phishing is a common strategy. Call scams are common around the world. The invader impersonates a representative from your local bank or your ISP and tries to steal details from your mouth.
Spear Phishing
Usually, phishers send mass e-mails, but they target a specific person they have researched before. Therefore, the targets believe the attackers even more because they have all the knowledge a bank or official may have.
88% of corporations overall experienced spear-phishing attempts in 2019.
Nigerian Prince Scam (419 Scams)
It is one of the oldest and commonly employed phishing techniques. The attacker impersonates a Nigerian Prince who needs a bank account to get his money out of the country. They promise compensation for the target’s troubles. They are also called 419 Scams because Article 419 of the Nigerian Constitution deals with fraud and deceit.
After declining in 2019, phishing expanded in 2020 to represent 1 in every 4,200 e-mails. $17,700 is lost each moment because of a phishing assault.
Ransomware
As the name suggests, Ransomware is a type of malware that holds your files hostage to extort ransom from you. A computer can get afflicted with ransomware, and it will encrypt your files and ask you for ransom in return for access to your files. Ransomware is gradually becoming a serious security threat.
Ransomware can attack a person with a plethora of methods. One may get it from an unsolicited e-mail or a download off the internet. There are multiple types of ransomware:
Scareware
A type of ransomware that gives un-controlled pop-ups about a grave danger to your computer: a link to a website will be provided to fix the issue. The hackers will use the fake website for phishing your data.
Screen Lockers
Screen lockers’ primary goal is to freeze your screen. The hacker may send you a link to be followed or a number to be called to unfreeze it. If the target is persuaded, he will become a target of phishing.
Encrypting Ransomware
These are the nastiest types of ransomware that hold your files in return for money. The target will either have to delete their files or pay the ransom. Since no protection software can return your files to you, this is a bane for most people. Therefore, even if you pay the ransom, there is no guarantee that the hackers will return your files.
The same is the case with WordPress websites. They can be encrypted, and the WordPress website hacker can demand a ransom in return. All of this with little guarantee that the hacker will return your WordPress website to you.
On average, just 5% of organizations’ folders are appropriately secured. The ransomware demands rose 33% in 2020 more than in 2019, to $111,605.
Epilogue
Various website security threats exist which can harm your WordPress website in several ways. One must tend to these security threats as soon as possible. Data breaches have become relatively common due to a rise in the number of hackers and ill-managed WordPress websites. These threats have already caused enough damage, and the number of attacks is increasing exponentially. Website developers or managers should be vigilant about their WordPress websites so that their WordPress websites do not get attacked. In the case they do get attacked, they should be able to defend their WordPress websites.

